
Security Information Event Management
Reduce Vulnerability & Risk with Rapid Detection & Response
What is a SIEM and why does every IT department need it?
Security Information Event Management SIEM solutions will be far more than just an information platform, they will expanding to include compliance reporting and logs from firewalls and other devices, as well as user and entity behavior analytics (UEBA).
How many different vectors are you capable of monitoring? Here is just a sample of the data sources you need to start tracking and securing the enterprise from cybercriminals. Security Information Event Management systems will aggregate logs into a centralized repository and can perform automated analysis on those logs to discover trends and detect anomalies.
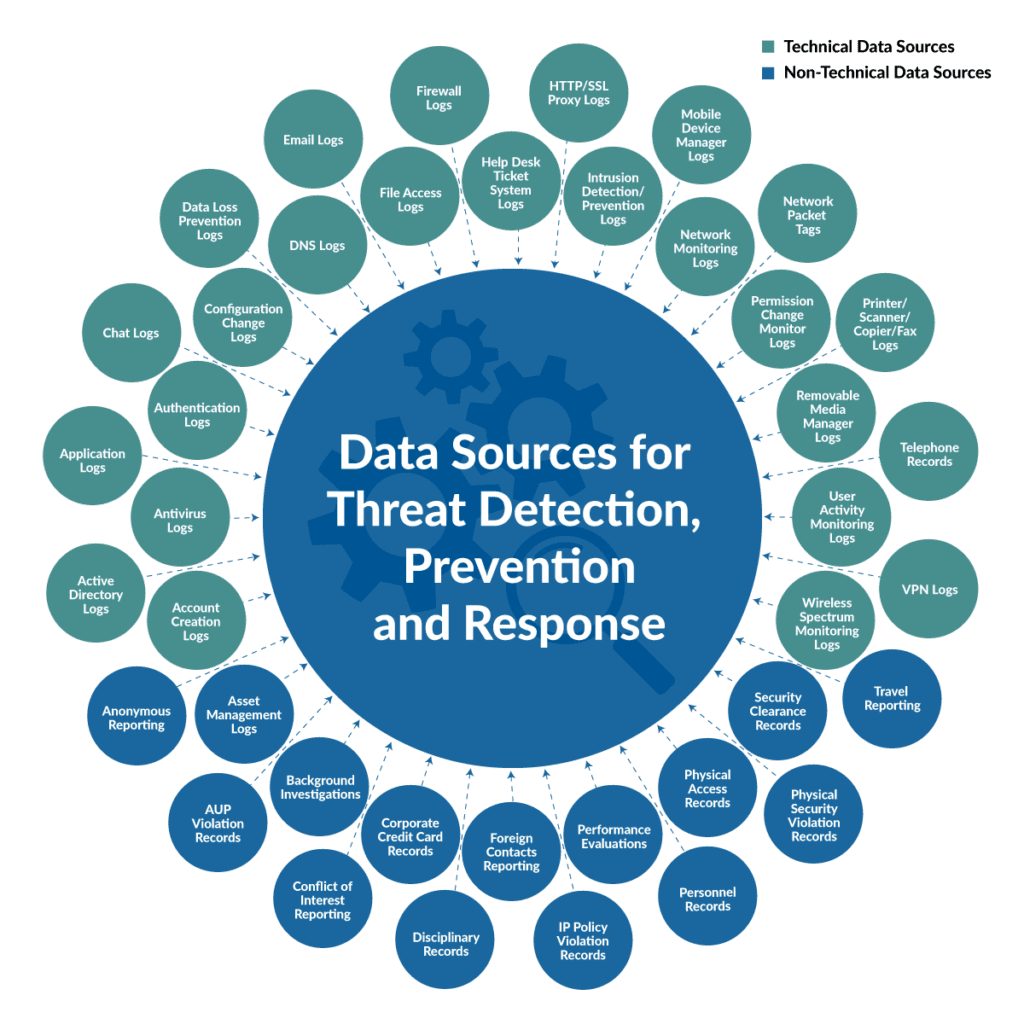
InData’s Security Information Event Management system or SIEM system provides an additional method for the collection, aggregation, and consolidation of logs from many types of devices. The SIEM leverages baseline and configurable rules to correlate the logs and provide real-time incident-based alerting/notifications.
SIEM systems can help detect anomalies, which may lead to discovering potentially malicious insiders. The systems baseline and correlation perform a first order of rudimentary analysis that presents a more organized view of the raw log data. SIEM systems also aid in investigations by providing evidence that can be used for both internal incident response and external legal actions. Logs from critical devices are sent to the SIEM for centralized storage and analysis.
Analytics
Analytics tools extend the query and alert the functionality of the SIEM. They can implement advanced machine-learning and statistical techniques to uncover and alert on anomalous activity based on the following:
- threshold/volume-based anomalies
- user/role-based activity baseline
- previously unidentified patterns and trends
InData can also provide additional advanced visualization capabilities such as charts and graphs that can make anomalies more visually apparent.
Digital Forensics and Investigations
Digital forensic science is the use of scientifically derived and proven methods toward the preservation, collection, validation, identification, analysis, interpretation, documentation, and presentation of digital evidence derived from digital sources for the purpose of facilitating or furthering the reconstruction of events found to be criminal or helping to anticipate unauthorized actions shown to be disruptive to planned operations.
Organizations should have digital forensic tools to support investigations and allow a properly trained individual to preserve, collect, and analyze digital artifacts on a system or device. These tools can be used to assist in the investigation of malicious insider actions and provide the necessary evidence for potential legal actions.
Documenting Roles
Having a process in place that is continually practiced and played out makes for a strong security team. InData helps bring that structure to help your existing IT Team respond to critical security anomalies. We work with your Team by doing the initial investigation and bringing forward areas that need near-term or immediate attention.
SIEM Summary
InData can help cover the blind spots and reduce the probability of a costly data breach. We offer co-managed security or fully managed services to meet your company’s needs. To learn more about InData’s SIEM program contact us online or email [email protected] for more information.
